When it comes to networking, private IP addresses are the unsung heroes that keep our internal systems running smoothly. Among these, the 10.0.12 range stands out as a versatile and widely used block. Whether you’re managing a small home network or a sprawling enterprise, understanding the nuances of 10.0.12 can significantly enhance your network’s efficiency and security. In this blog post, we’ll explore everything you need to know about 10.0.12, from its technical underpinnings to its practical applications, and why it’s a cornerstone of modern networking.
What is 10.0.12? A Quick Overview
The 10.0.12 range falls under the 10.0.0.0/8 private IP address block, as defined by RFC 1918. This range is reserved for internal use within private networks and is not routable on the public internet. This means devices with 10.0.12 addresses can communicate seamlessly within their network but require Network Address Translation (NAT) to access the internet.
For example, a device with the IP 10.0.12.16 can send requests to 10.0.12.17 without issue, but to access a website like Google, it needs to go through a router that translates its private IP into a public one.
Why 10.0.12 Matters in Networking
1. Scalability and Flexibility
The 10.0.0.0/8 block offers a staggering 16.7 million IP addresses, making it ideal for large organizations. Within this, 10.0.12 can be further divided into subnets, allowing for hierarchical network design. For instance:
- 10.0.12.0/24: A subnet with 254 usable addresses for a specific department or location.
- 10.0.12.16/32: A single device, like a server or printer.
This flexibility ensures that even the largest networks can be organized efficiently.
2. Enhanced Security
Since 10.0.12 addresses are non-routable on the internet, they’re invisible to external threats. This provides a layer of security by default. For example, a hacker scanning the internet won’t see your 10.0.12.16 server unless they breach your NAT gateway.
3. Cost Efficiency
Using private IPs like 10.0.12 allows organizations to conserve public IPv4 addresses, which are scarce and expensive. A single public IP can serve thousands of private devices via NAT, significantly reducing costs.
Read Also https://prepare4test.com/cisco-ios-12-0-10-what-you-need-to-know/
Challenges and Risks of Using 10.0.12
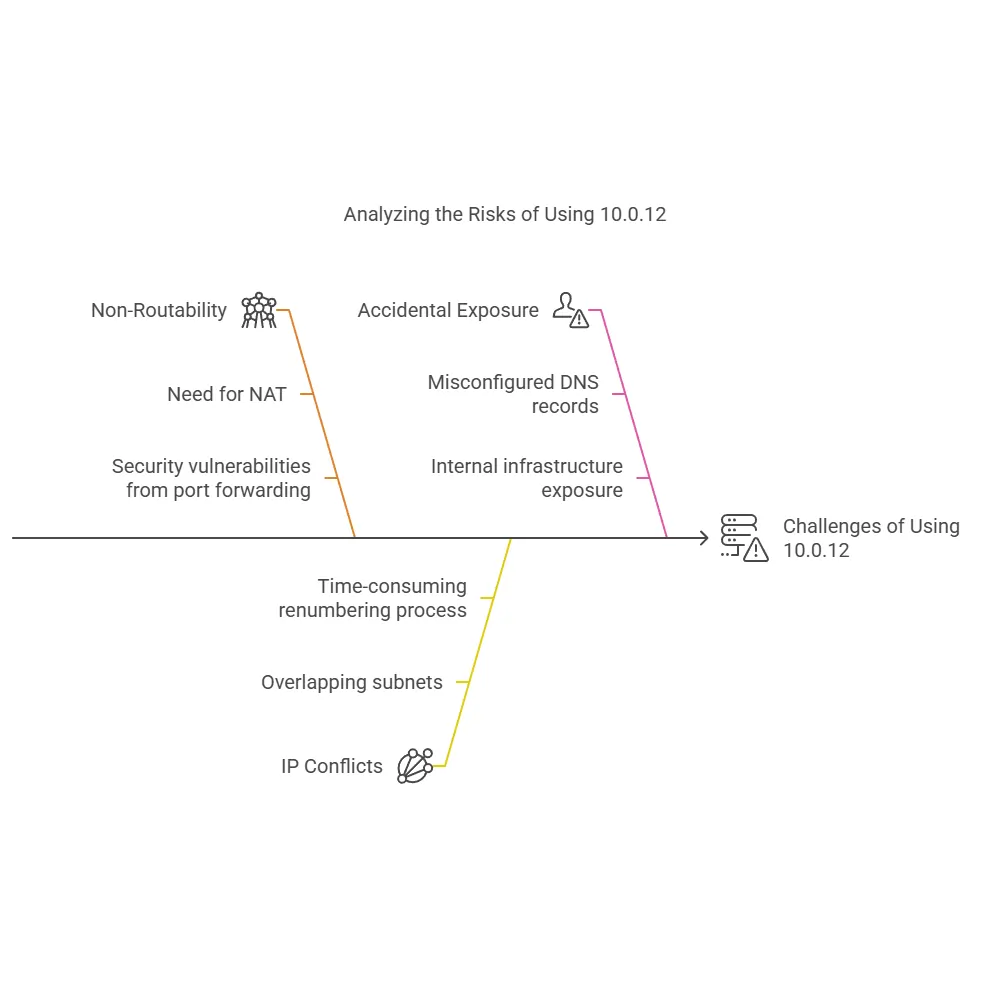
While 10.0.12 offers numerous benefits, it’s not without its challenges:
1. Non-Routability
Devices with 10.0.12 addresses can’t directly access the internet without NAT. Hosting public-facing services (e.g., a website) on 10.0.12.16 requires complex configurations like port forwarding, which can introduce security vulnerabilities if not managed properly.
2. IP Conflicts in Merged Networks
When two organizations with overlapping 10.0.12 subnets merge, IP conflicts can arise. Resolving these often requires renumbering, a time-consuming process that can disrupt operations.
3. Accidental Exposure
Misconfigured DNS records that point to private IPs like 10.0.12.16 can inadvertently expose internal infrastructure to the internet. Attackers can use these records to map your network and launch targeted attacks.
Best Practices for Managing 10.0.12 Networks
To maximize the benefits of 10.0.12 while mitigating risks, follow these best practices:
1. Implement Network Segmentation
Divide your 10.0.12 range into smaller subnets to isolate different departments or functions. For example:
- 10.0.12.0/27 for servers.
- 10.0.12.32/27 for user devices.
This reduces the risk of lateral movement during a breach.
2. Enforce Strict Firewall Rules
Configure firewalls to allow only essential traffic to 10.0.12 devices. For example, only permit HTTPS (TCP/443) access to a web server at 10.0.12.16.
3. Regularly Audit DNS Records
Use tools like Attack Surface Intelligence to scan for public DNS records pointing to private IPs. Removing these records prevents reconnaissance by attackers.
4. Consider IPv6 for Future-Proofing
For long-term scalability, explore IPv6 Unique Local Addresses (ULAs), which eliminate the subnetting constraints of IPv4.
Real-World Applications of 10.0.12
1. Enterprise Networks
Large organizations often use 10.0.12 for internal servers, printers, and user devices. For example, a company might allocate:
- 10.0.12.0/24 for its headquarters.
- 10.0.13.0/24 for a remote office.
This hierarchical approach simplifies management and improves routing efficiency.
2. Home Networks
Even in smaller setups, 10.0.12 can be useful. For instance, a home router might assign 10.0.12.2 to a smart TV and 10.0.12.3 to a gaming console, ensuring seamless communication between devices.
3. Virtual Private Networks (VPNs)
When employees connect to a corporate VPN, they’re often assigned 10.0.12 addresses. This allows them to access internal resources securely, even from remote locations.
Case Study: A Cautionary Tale
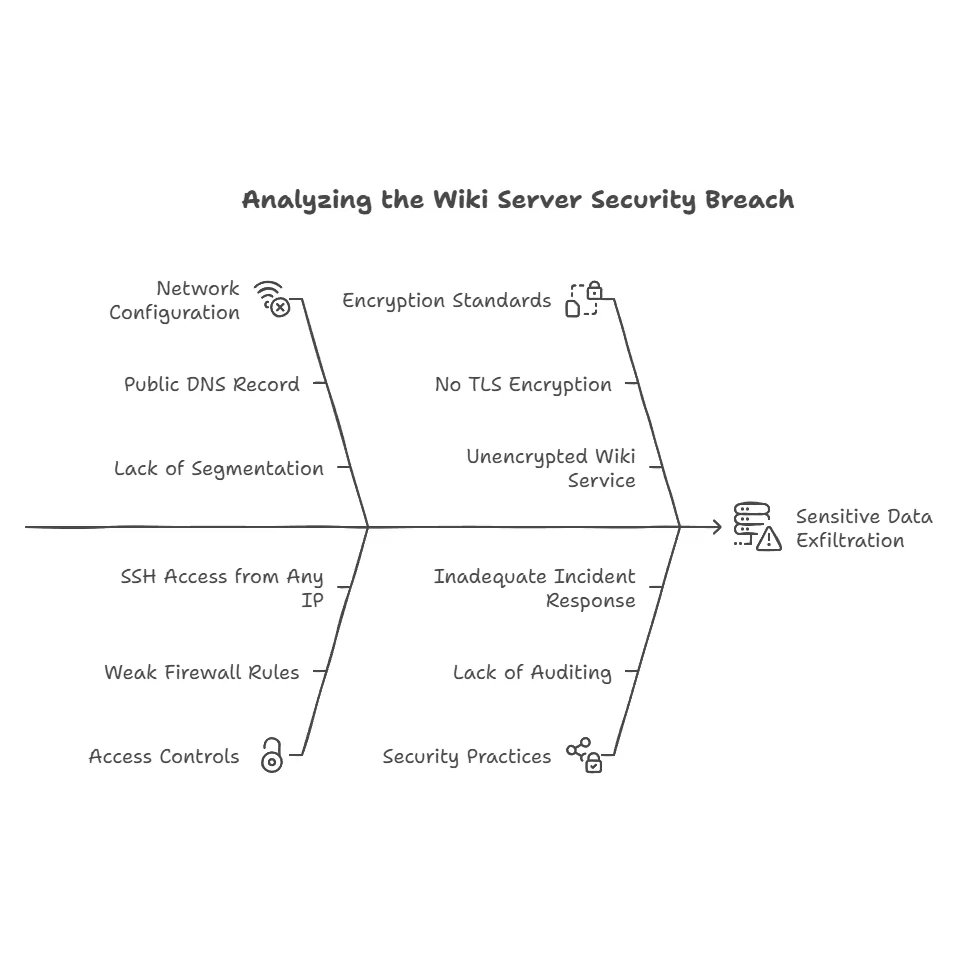
A medium-sized enterprise configured its internal wiki server at 10.0.12.16 but accidentally published its DNS record publicly. Attackers discovered this record, targeted the server with credential-stuffing attacks, and exfiltrated sensitive data. Post-incident analysis revealed:
- Absence of subnet segmentation.
- Weak firewall rules permitting SSH access from any internal IP.
- Lack of TLS encryption on the wiki service.
This incident underscores the importance of isolating critical servers, enforcing strict access controls, and auditing DNS records.
The Future of Private IP Addressing
While 10.0.12 remains a cornerstone of IPv4 networking, the future lies in IPv6. With its vast address space (e.g., fd12:3456:789a::1), IPv6 eliminates the subnetting constraints of IPv4 and introduces features like Unique Local Addresses (ULAs), which embed a 40-bit random global ID to prevent collisions during network mergers.
People Also Read https://prepare4test.com/product-category/cisco/cisco-certified-technician-routing-switching/
Key Takeaways
- 10.0.12 is a versatile and scalable private IP range ideal for internal networks.
- It offers enhanced security, cost efficiency, and simplified internal communications.
- However, it requires careful management to avoid risks like IP conflicts and accidental exposure.
- Best practices include network segmentation, strict firewall rules, and regular DNS audits.
By adhering to these guidelines, organizations can harness the full potential of 10.0.12 while mitigating its pitfalls.


